Protecting Business Data
Assets of an organization must be protected to ensure their long-term viability. The tangible assets of a business or organization are obvious: factories, vehicles, office buildings, and computers are something we see every day. Intangibles, such as business data, are less apparent but can be just as valuable. Although we protect tangible assets with an array of measures from physical security to insurance, those measures are not always appropriate or sufficient for protecting business data. There are, however, well-established best practices for ensuring the integrity and reliability of business data. This article summarizes some of these best practices, with an emphasis on understanding the
- Business value of data
- Cost of losing business data
- Need for continuous protection of data
- Need for disaster recovery planning
Like tangible assets, business data is critical to the proper and efficient operation of an organization and should be protected appropriately.
The Business Value of Data
How does one place a value on business data? One way to answer this question is to look at where business data is generated and how it is used.
Operational Data: The Leading Edge of Business
Consider the business operations that depend on reliable, accurate data. Fulfilling product orders depends on a wide range of information including inventory, customer information, order tracking, credit status of customers, payment history, billing arrangements, and other contractual agreements. Managing employees entails tracking payroll, tax, job assignments, training history, and performance reviews. Financial managers work daily with accounts payable and accounts receivables, monitor the general ledger, and provide budget management support to line managers. It is difficult to envision a modern business process that is not, in some way, data dependent. Much of the data collected in the course of these business operations is also of direct value to customers.
The drive for more efficient operations has contributed to the evolution of more streamlined supply chains. Customers can share data about inventory levels to trigger automatic orders to replenish supplies. Salespersons can analyze customers' buying patterns to find sales promotions that best fit a customer's needs. Suppliers can even become information providers to customers by offering detailed information about account history and trends that can better help the customer understand their overall buying patterns. Data generated within a business is often of value to customers, supply chain providers, and other business partners.
Business Intelligence Data: Understanding the Big Picture
Data about one business operation is useful; combining data from multiple operations is even better. Business intelligence (BI) is a term applied to managing data in such a way that executives, managers, analysts, and others can make informed decisions about the business. Unlike operational systems that maintain detailed information about a single operation, such as inventory or cash flow, BI systems combine data from multiple operational systems to give a broader picture of aggregate business functions. For example, a marketing analyst formulating a new promotion might need data about
- Past product sales by region and customer industry code
- Revenue margins by product category
- Sales quantity information by time period
- Information on seasonal variations in purchasing patterns
- Production and inventory forecasts for the next 3 to 6 months
It is highly unlikely that any single operational system will have all this data. Operational systems are designed and tuned to address particular types of information management needs for specific business processes, which are not necessarily the same needs of executives and analysts. Typically, a data warehouse or data marts are created to collect and manage data from multiple operational systems to support decision makers For example, as shown in Figure 1, operational data from a variety of applications is collected, coordinated, and analyzed to produce high-level, aggregated views of key business information.
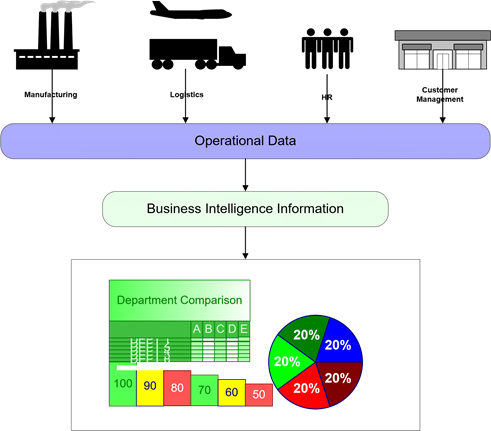
Figure 1: Business data begins with and supports core operations, but it is also valuable when combined with other operational data to provide a comprehensive view of business functions.
One result of the use of BI systems is that organizations have even more data to manage. BI systems derive new information from existing data sources, creating a new class of data that must be protected.
Both operational and BI data can offer insights into current operations, help identify weakness in processes, and provide needed information to revise and innovate. New and innovative business processes can come in a "Eureka" moment when someone of keen insight fortuitously realizes a new opportunity. A more reliable method for innovating is to understand operations and opportunities; that understanding comes from comprehending what business data has to say.
Business data is an intangible yet valuable asset to organizations. It is the foundation of many business processes and the grist for the innovation mill. Just how valuable it is can become apparent when it is not available.
Cost of Losing Business Data
The full cost of losing business data stems from both immediate and long-term implications of the loss:
- Disruption of operations
- Cost to consumers
- Reduced information about customers and markets
In the short run, if business data is unavailable, it immediately impacts operations. Imagine a server running a customer database suffers a failure and is unavailable. Customers might not be able to place orders, check account statuses, verify shipping information, or get answers to billing inquires. In short, they are unable to conduct even the simplest business transaction with the company.
In the mid-term, lack of customer business data can affect operations outside the single organization. With tight supply chains, a failure in your system can have a direct impact on customers' ability to deliver to their customers. If your customer cannot tell their customers when a shipped part will arrive, how much it will cost, or how many are available, how are they to conduct their business? Modern supply chains work because business operations are reliable; when the essential characteristic is lost in one part of the supply chain, it can have ripple effects through the rest of the supply chain.
The long-term implications of a lack of business data can be severe as well. With reduced aggregate information about customers, buying trends, and inventory levels, it is difficult to formulate an efficient strategy for running a business. Fortunately, there are well-established practices for protecting business data and responding to disruptions in business services.
Continuous Protection of Data
A simple precaution is at the heart of many data protection plans: make a copy of the data. In spite of its simplicity, this operation entails surprisingly complex implications. To see these, consider the different ways you can back up data. There are four basic types of backups:
- A full backup makes a copy of all data. It is the simplest scheme to implement and manage. If recovery is required, a backup administrator copies needed files from the backup tape or disk.
- An incremental backup makes copies of data that has changed since the last backup. This can reduce the time and storage needed to perform backups because only changed data is copied each time an incremental backup is made. For example, if a full backup is made on Monday and only one file is changed on Tuesday, only that one file is backed up in the incremental backup. A drawback of incremental backups is that to restore files after a failure, one must restore the last full backup and all the incremental backups made after that full backup.
- A differential backup is similar to an incremental backup but copies all data that has changed since the last full backup (incremental backups make changes only since the last incremental or full backup). Differential backups can require more storage space than incremental backups, but they reduce the time and complexity of restore operations.
- Continuous backups make copies of files each time they are changed. This ensures that if there is a failure, a very recent copy of the data is available to restore. If full, incremental, or differential backups are made in the middle of the night and a server crashes near the end of the business day, a full day of work may be lost. This is not the case with continuous backups.
Each of these backup models has advantages and disadvantages that tend to involve tradeoffs between the amount of storage space required for backups, the time required to recover data, and the amount of redundancy needed to ensure that if a backup set fails during restoration, another backup set is available to restore a system to the point of failure.
It should be noted that although we often speak generically about backing up files, specialized applications such as databases and email servers have idiosyncratic backup and recovery operations. A database, for example, may store user data in a series of files. Each of these files may store hundreds of database tables each of which contains data on a particular item, such as customers, products, or payroll history. When a database administrator performs a restore, she might only want to restore a single table, not an entire database file. Similarly, email systems may store entire inboxes or email folders in a single file and a user may need only a single attachment restored, not an entire folder. For these and similar applications, specialized backup and restore software is required for efficient data protection (see Figure 2).
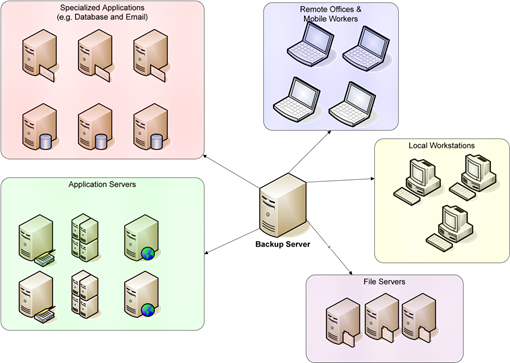
Figure 2: Backup systems are expected to support a variety of clients with distinct requirements.
Backup systems might have to serve multiple types of client devices, ranging from local workstations to high-availability application servers. When considering backup solutions, consider these factors:
- Are you running high-availability applications that require redundancy and failover backup servers? These types of applications require continuous access to data, so a combination of redundant storage arrays and continuous backup applications may be required.
- Will remote networks, such as satellite offices, be backed up centrally? If so, backup software designed to support and manage remote backups without placing inordinate demands on network bandwidth is recommended.
- Does critical data reside on laptops and desktops? For example, salespersons might keep copies of contracts, orders, and other customer documentation on laptops. If so, a backup solution for the business should accommodate the need for continuous backup of critical files on these devices.
In addition to supporting selective recovery of files and data, backups are also part of the solution for large-scale disaster recovery.
Disaster Recovery
One only needs to think of businesses along the Gulf of Mexico coast during hurricane season to appreciate the need for a disaster recovery plan. The specific details of each business' requirements will vary, but a sound disaster recovery strategy generally includes
- A plan for establishing business operations in an alternative site
- An understanding of the time required to re-establish operations at the alternative site
- A plan for moving operations back to the original site when conditions allow
- An estimate of the cost to operate under these conditions
The goal of such a strategy is to keep the business functioning during times of disaster, and part of this task is preserving business data, enabling business operations, and ensuring that normal operations can be restored as soon as possible.
Summary
Business data is a valuable asset to any organization. Both operational and business intelligence data are essential to the long-term viability of a business. In many cases, this data is also of substantial value to business partners and customers. Preserving the integrity of business data requires a reliable backup system that meets the needs of your business and accommodates the network, server, and workstation infrastructure in place. Fortunately, well-established best practices and mature backup solutions are available to help ensure that business data is protected against the risks faced by all organizations.