Best Practices for e‐Document Collaboration and Exchange
Efficient collaboration and information exchange stems from a combination of suitable technology and management acumen. Without both, we risk either a sound technical solution that never delivers on expected return on investment (ROI) because of poor implementation or a deficient application that will never deliver essential collaboration services in spite of an implementation team's best efforts. The previous chapter discussed issues surrounding collaboration and information exchange technology; in this, the final chapter of this guide, we turn our attention to the management aspects of collaboration:
- Aligning content and forms management with business strategy
- Identifying areas for more efficient content and forms management
- Enabling collaboration through supportive business processes
The structure of the chapter follows a top‐down approach, which can be used to help deploy collaboration technologies in your business. First, we identify collaboration and information exchange in major business operations and assess how well it aligns with broad business strategy. Next, we identify potential areas for more efficient content and forms management, especially in areas deemed essential for the business strategy. Then, with target areas identified, we move on to implementing solutions following a seven‐step framework described in detail.
Content and forms management and even collaboration itself is not the ultimate goal of our efforts. Efficiently executing business or organizational strategy is our objective, and collaboration services are a means to meet that goal. With that in mind, we begin with a discussion of aligning collaboration services with business strategy.
Aligning Content and Forms Management with Business Strategy
No well‐run business would buy a fleet of vehicles, rent several floors of an office building, or start construction on a manufacturing facility unless these expenditures were called for to meet an enterprise objective. Deploying enterprise software and revising business processes should be held to the same standard. Business strategies define the enterprise's objectives; content and forms management operations should be designed with those objectives in mind. This task is accomplished by first understanding the need for content and forms management with business strategy, then prioritizing changes according to priorities established by business objectives.
Understanding the Need for Collaboration and Information Exchange in Key Business Operations
Collaboration occurs in both formal and informal ways, and each has its own particular characteristics that should be accommodated when deploying new tools for collaboration and information exchange.
Formal Information Exchanges
Take, for example, a formally‐structured purchase requisition process. An employee needs a license for PC software, so she fills in a requisition form with information such as her name, department, product requested, purchase price, and justification for the purchase. The form is routed to her manager who signs it, adds an account number to charge, and forwards to purchasing. A staff member in the purchasing department adds other information to the form, such as the vendor to use and purchase date. The form is then filed and retained according to the company's document retention policy. Salient features of this process include:
- The sequence of steps from start to finish is fixed and known to all participants.
- The type of information shared is fixed and includes names, dates, account numbers, and relatively short free‐form text descriptions.
- The process is governed, in part, by companywide policies, such as document retention policies and audit requirements.
Now, compare that example to an informal collaboration process.
Informal Information Exchanges
A company is considering redesigning a once‐popular product that is now showing a decline in sales. Multiple teams form to better understand the reason why. One group of marketing analysts develops a review of competitive products while another group collects competitive intelligence on the product manufacturers. They collaborate using a shared directory. Quality control engineers summarize quality assessment data on the product and share it with a member of the marketing team via email. Various team members have a conference call to assess the data they have so far. They conclude additional customer data would be useful but there is no budget for a survey or focus group. An intern with some programming skills volunteers to collect data from opinion Web sites. The marketing teams open their shared drives to the quality control engineers and intern to better facilitate exchange of documents.
This example of an informal process is characterized by:
- No fixed sequence of events; some steps in the collaboration process happen in parallel.
- The type of information shared includes long, unstructured texts such as reports as well as statistical data on customer opinions.
- The process is adaptive and solves problems as they arise, for example, by finding a substitute for a customer survey that is not practical.
Informal processes are ad hoc by nature, but there are ways to optimize these by focusing on the applications that support them. For example, information overload is a common problem when searching for documents and other forms of content. Two‐ or threekeyword searches often return more results than we can reasonably expect a user to review. By adding metadata attributes to documents in the repository, content creators can provide additional information about documents, highlighting key concepts, version information, and revision histories. These additional attributes can be used to restrict searches to a smaller set of results. Formal information exchanges offer opportunities for several types of optimizations that are described below.
Need for Both Formal and Informal Exchanges
Both formal and informal information exchanges have a role in businesses, governments, and other organizations. One is not better than the other any more than a hammer is a better tool than a screwdriver. Formal information exchanges support well‐defined business processes that are repeated and follow a relatively fixed pattern. Informal information exchanges tend to emerge to address the needs of complex problems with varying requirements, such as determining why a product's sales are in decline, designing a new customer service application, or generating ideas for a new strategic initiative.
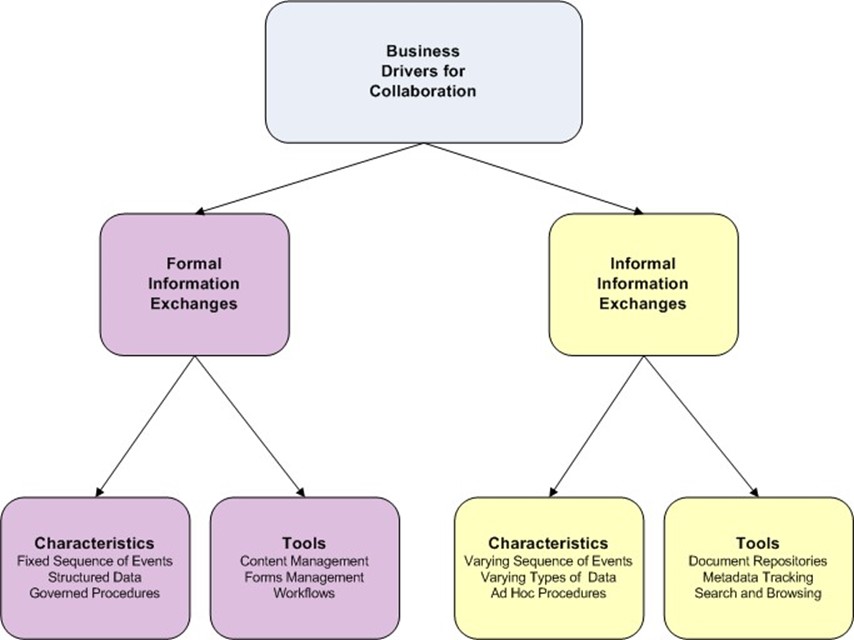
Figure 4.1: Information exchanges can be broadly categorized as formal and informal. Both can be used to meet the needs of business requirements. Each type has its own defining characteristics that require particular types of applications.
In general, we want to prioritize collaboration and content management services according to the priorities of business drivers. We also want to make sure we provide the right kinds of applications to support the needed kind of collaboration. Formal information exchanges are well served with forms management and workflow systems. Informal exchanges need content repositories, search tools, metadata tracking, and other methods for finding targeted information and browsing to understand the range of information available.
Optimizing Formal Information Exchange
Formal information exchanges are used repeatedly, so it's worth optimizing those processes. In this section, we will focus on tips to identify potential areas of improvement in content and forms management. In particular, we will consider how to improve formal information exchanges by:
- Detecting unnecessary delays in the collaboration and information exchange process
- Revising the existing review and approval processes
- Detecting overlap and redundant processes
- Merging overlapping workflows
- Replacing inefficient paper‐based processes with electronic form‐based processes
These general approaches can help with a broad range of formal information exchange processes because they share the characteristics previously outlined that lend themselves to these types of efficiencies.
Detecting Unnecessary Delays in the Collaboration and Information Exchange Process
The potential for unnecessary delays in information exchange occur for one of two reasons:
- First, when we unnecessarily require a step in the process that could be eliminated without adversely affecting the overall process, it is an unnecessary dependency.
- Second, when we schedule steps in sequence when they could be done in parallel, it is a lack of parallelism.
Let's consider an example of each and see how relatively simple changes in the process can lead to a significant improvement in efficiency.
Unnecessary Dependencies
An insurance claims processing department in a hospital has a long‐established procedure for handling claims:
- The department receives paperwork describing a patient's treatment from a physician
- A claims processing clerk combines the physician's paperwork with the patient's insurance information, which was collected when the patient was admitted
- The clerk proceeds to enter personally identifiable information and treatment information into an insurance claim form
- The clerk sends the completed form to a supervisor on duty for review
- The supervisor reviews the forms and submits them to the appropriate claims coordinator for the insurance company receiving the claim
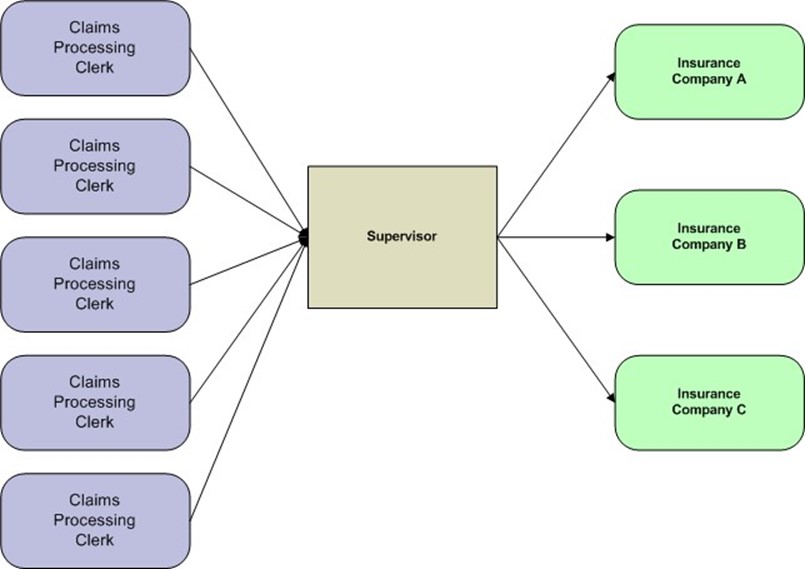
Figure 4.2: The supervisor review step is a bottleneck and delay in the insurance claims process workflow. If the tasks performed by the supervisor could be automated, an unnecessary dependency could be removed.
The process is reasonable. All the information that is needed to fill out the claims form is collected before filling out the claim. The clerk extracts needed information and puts into a standardized form; the supervisor reviews the form for errors and omissions and then sends it on to the insurance company. This is precisely how the process should have been handled when claims processing was primarily paper‐based; however, the hospital now uses electronic forms, which reduces the need for one time‐consuming step.
The reason the supervisor reviews the forms is to ensure all the necessary information is in place, the codes that are used are reasonable for each field, and the dates make sense (for example, the discharge date is not before the admitted date). Electronic forms can do this step automatically. When forms are created, the designer can specify lists of acceptable codes for particular fields, identify fields that should not be left blank, and define rules about the values in certain fields, such as the start date cannot occur after the end date. Step number 4 has become an unnecessary dependency and can be eliminated.
Lack of Parallelism
Another potential delay occurs when steps that could be done in parallel are instead done sequentially. For example, a project manager may submit a requisition for a new server. Company policy directs that when a new server is to be acquired, the request must be reviewed and approved by:
- The department manager who is responsible for paying for the server. This manager must ensure adequate funds are available.
- The IT manager responsible for servers. This manager is responsible for ensuring the server configuration meets company standards.
- The purchasing manager who must verify that bidding procedures were followed and the server is to be purchased from an approved vendor.
If the typical workflow for this procedure is to send the request to the department manger who then forwards it to the IT manager who then sends it on to the purchasing manager, then we have a lack of parallelism.
The three managers all have independent responsibilities. It does not matter, at least in the strictest sense, to the IT manager if there are sufficient funds in the department's budget. The purchasing manager need not concern herself about the detailed specifications of the server. Yet, if the typical workflow is followed and the department manager is out on vacation, it could be a week before it moves to the IT manager who, by that time, may be out of the office at a conference, adding further delay. A better approach is to allow the three managers to review a shared version of the document and add comments to it. The project manager could then see comments as they are added and can address issues as they arise rather than waiting for all three managers to finish their reviews.
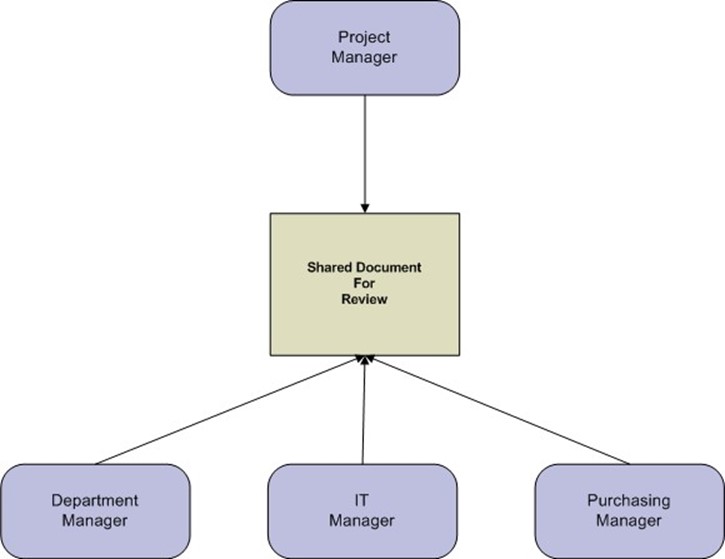
Figure 4.3: Parallel reviewing avoids bottlenecks and allows the person submitting the form to receive incremental comments instead of waiting for all reviewers to comment.
Revising Existing Review and Approval Processes
As the previous examples show, the review and approval process is a prime target for optimizing information exchanges. It is particularly important to review approval procedures when a workflow changes or a new application is introduced.
For example, a workflow may require a review by someone in the finance office to verify fund levels are sufficient to cover costs of purchases. This step would make sense in a time when department managers did not have direct access to up‐to‐date balances in their budgets. If managers can open a simple reporting application that shows them their account balances, then responsibility for checking those balances can shift to the managers. This would eliminate a step in the workflow and relieve the finance office staff to attend to other tasks.
Detecting Overlap and Redundant Processes
It is not uncommon to have the same procedure performed multiple times in a workflow. For example, a project manager might verify a vendor is still on an approved vendor list before sending a request through for processing. The department manager and purchasing manager may do the same thing. This kind of redundancy could be reduced by modifying forms to include a check box and initial field to be filled out by the first person who performs the check.
Another potential area of overlap comes with the requiring redundant information in a form. For example, one section of a form may be labeled Purchasing Department and contain information that must be filled out by that department. Some of that information may have already been provided in another section filled out by the person originating the form. An automated form could be used to copy information from one section of the form to the other, saving the purchasing department an additional step.
Now we could argue that the same information should not be entered twice, but forms can be long and complex. We do not want to force reviewers to unnecessarily jump from one end of a multipage document to another. The design principle of not duplicating data works well when designing databases, but we humans are the ones working with the complex forms, and usability concerns should guide form design. (A backend database may still store only a single copy of the information but display it in multiple places in the form so that there is not even a need to choose between database design principles and usability principles.)
Merging Overlapping Workflows
Sometimes redundancies can only be detected by looking at a series of workflows. For example, the IT department may have a workflow for processing requisitions and the finance department has another workflow. They are independent, and analysts trying to optimize one may miss efficiencies that could occur if the two workflows were combined. The goal in this case is to look at the full business process (for example, a purchase requisition) rather than the separate workflows that are currently in place to implement that workflow.
When evaluating the feasibility of merging overlapping workflows, consider how a combined workflow might introduce unwanted side effects:
- Constraints that actually slow the process. This can occur in cases where separate workflows could be performed in parallel but the combined steps are done in sequential order.
- Problems sharing information across work units, such as violations of policies in place to ensure regulatory compliance. In the case of a hospital claims processing example, there may be protected healthcare information that can be shared between doctors and insurance claims processors but not with finance department analysts that generate management reports on claims processing.
- Potential bottlenecks in the approval process. If managers from multiple departments have to approve a form, there is the potential for a deadlock if two or more managers decide to wait for the other manager(s) to approve the form. In such cases, it is important to define the sequence of approvals when redesigning the workflow.
Merging workflows can improve the overall efficiency of a business process but care must be taken to avoid unintended consequences such as these. Redesigning a workflow on a whiteboard and walking through a variety of scenarios is one way to uncover potential problems.
Replacing Inefficient Paper‐Based Processes with Electronic Form‐Based Processes
Replacing paper‐based workflows with electronic form‐based processes enables a number of efficiencies:
- Employees can access forms even when they are out of the office
- Reviewers can see each other's comments when a shared copy is used for review
- Automatic data entry checks can reduce the need for manual review of forms and allow users to catch clerical errors immediately
- The most efficient workflow process can be defined and enforced with the right forms management software
- Compliance may improve with the use of standardized workflows. For example, documents can be automatically archived according to compliance requirements
Clearly moving from paper‐based to electronic form‐based information exchanges can result in more efficient operations. As we noted earlier in this chapter, it takes a combination of the right technology and the right management plan to get the most out of this process. In the next section, we will outline a framework for implementing and maintaining electronic forms‐based information exchanges.
Establishing Supportive Business Processes: A 7‐Step Framework
Moving from ubiquitous paper‐based information exchanges to electronic forms and collaboration can look like a daunting task, but there are some steps we can take to improve the process and reduce the chance of missing opportunities, introducing the wrong technology, or getting bogged down in delayed implementations. The following list highlights the seven steps of a framework for moving from paper‐based to electronic‐based information exchanges:
- Define formal workflows and approval processes
- Identify applications needed to support collaboration
- Set security policies
- Review archival processes
- Deploy e‐document technology to the desktop
- Educate and train users
- Monitor and tune on an ongoing basis
As with other frameworks and methodologies, these steps map out key tasks. For some businesses and organizations, some steps will go quickly while others may find that significant time is needed to fully execute one of these steps. In all cases, though, start each step by trying to assess the scope of the step and work incrementally to complete the step.
Defining Formal Workflows and Approval Processes
The first step is to understand the business requirements for formal and informal information exchanges. Identifying formal processes is often easier because they are often part of the routine operations of a business. They range from the relatively simple processes, such as collecting time cards, to the more complex, such as updating revenue and expense projections for business units. In the early stage, one should focus on identifying as many workflows as possible and documenting basic characteristics, such as those shown in Table 4.1. The goal at this point is to understand how many workflows are in existence, who is responsible for them, how critical are they (that is, if the workflow was shut down completely, how adversely would it affect the business?), and the relative priority for each.
Name | Description | Responsible Department | Number of Participants | Criticality | Priority for Improving | Formal or Informal |
Time Card Reporting | Collects each employees' leave time | HR | 1000 | Medium | Medium | F |
Purchase Requisition | Process for all purchases over $100 | Finance | 200 | Medium | High | F |
Working Injury Report | Documents workplacerelated injuries | HR | 100 | High | High | F |
Quality Control Review | Shares information about QA problems, customer complaints, etc. | COO Office | 20 to 30 | Medium | High | I |
Table 4.1: Example summary inventory of existing workflows in a midsized business.
Identify Applications Needed to Support Collaboration
With an inventory of formal and informal information exchanges in hand, we are in a position to determine the kinds of applications we will need to automate these processes.
Some commonly needed applications include:
- Document creation forms—Ideally, an application should support basic word processing functionality, collaborative review, advanced security measures (see later), and integration with workflow systems.
- Data collection forms—In order to avoid bottlenecks and delays, these applications should be accessible to average office workers; programming skills should not be required. Forms should support basic data integrity checks and provide a mechanism for saving data to a database.
- Workflow management systems—These applications are used to route forms following a well‐defined policy. For example, a time card form could send employees' time cards to their managers for approval before sending them to Human Resources. In another case, a purchase requisition above a fixed amount would be routed to an executive for approval even though a department manager had already approved it.
- Management and compliance reporting support—Reporting systems can ease the burden of complying with regulations by providing the means to demonstrate the business is in compliance. Too often, being in compliance is not enough; we have to prove we are in compliance.
Businesses have the option of choosing these tools from a single or multiple vendors. This decision is a classic problem in information systems: do you choose best‐of‐breed applications or do you opt for a suite of tools from a single vendor to improve integration? When making such a choice, consider the following questions:
- Are "must have" features only available from some vendors?
- How much customization is required to make different vendor products work together?
- Will management reporting be available from a multi‐vendor solution?
- Will policies and security specifications have to be defined for each application or can they share one version?
- Do vendors support open standards so that information can be exchanged between systems provided by different vendors?
- Do suites contain more than you need so that you end up paying for unused features?
Of course, there is no single right answer for all businesses, but asking questions such as these can help determine an appropriate option for your business.
Establish Security Policies
Security policies address questions such as:
- Who should have access to particular content?
- How do we protect a document?
- How do we ensure reviewers and readers can trust the content of a document?
- How do we make sure our communications will remain confidential?
Since we are focused on collaboration and information exchange, we won't discuss the full span of IT security (that could take several books) but instead list policies that should be created and point out tools at our disposal to implement those policies. Policies should include when to require confidentiality measures, when to require digital signatures, and when to impose access controls on content that may be distributed outside the organization. For each of these policies, there are technical measures that can be used to enforce them:
- Digital signatures, which are used to ensure that we can trust the document was created by the purported author. This guarantee of non‐repudiation is important. Several types of well‐known security attacks use spoofing, the process of changing identifying information in a message to appear to be from someone else.
- Passwords, which prevent unauthorized users from viewing the content of a document.
- Document feature permissions, which restrict printing, copy and altering documents.
- Encryption, which is used to protect the confidentiality of information. Documents are encrypted with a digital key (a string of letters and numbers) and can only be read by someone with a decryption key.
- Digital rights management, which is used to enforce use and access agreements on content even if the content is sent outside an organization.
Security policies and related implementation methods can help preserve both the confidentiality and the integrity of content.
Reviewing Archival Processes
Electronic document management systems can provide a foundation for a more efficient and easily managed archival process than is available from paper‐based systems. As part of deploying electronic collaboration systems, we must remember to consider the full life cycle of the documents we are working with—this includes attending to archiving.
Organizations typically have document retention policies governing how long documents are retained and when or if they may be destroyed. One can imagine a worst‐case scenario when a large number of paper documents have to be maintained for an extended period of time. Actually, that worst case scenario can be even worse if the business continues to generate large volumes of documents that are added to the existing store of paper. If nothing else, electronic archiving could potentially lead to significant savings just in the cost of office space or other storage for retaining documents.
As part of the seven‐step framework for moving to electronic documents, assess the cost and effectiveness of your current archival practices. How much is spent on
- Labor to collect and archive relevant documents?
- Storage to hold these documents for future use?
- Quality control procedures and audits to ensure documents are properly archived?
- The opportunity cost of having management and staff talent dedicated to literal paper pushing instead of core business operations?
In addition to these costs, there are the risks associated with improper archiving. For example, a misplaced document may never be discovered until a court orders it to be turned over in a discovery proceeding. Failure to produce documents in a legal proceeding could lead to monetary fines or even a default judgment against the non‐complying party. Similarly, failure to comply with government or industry regulations can result in adverse findings during audits and possible fines.
Deploying e‐Document Technology to the Desktop
Another important step in the framework we are describing is deploying e‐document technology to the desktop. At first glance, one may wonder why this is any different from any other software deployment. In the narrow sense, it isn't. We can use software distribution systems to push applications and updates to the desktop, and use asset management systems to track licenses and configuration information. It is in the broader sense of deployment that we should note a few more considerations:
- Do not confuse e‐document technology with word processing software. They share some similar features but some efficiency and security features may not be found in word processors.
- The broader the base of users, the greater the potential benefits. Once the number of users reaches a tipping point or critical mass, adoption of a technology tends to accelerate. Providing e‐document programs to a broad user base can help realize a projected ROI. However, if too few users adopt the technology, it could put a damper on revising workflows and making procedures more efficient.
- Deployment to the desktop should be accompanied by review and approval processes that make use of the technology. This will promote adoption and again help realize anticipated efficiencies.
- Deploy security policies describe earlier when software is deployed. Do not wait— the security measures provided by e‐document technologies are one of the major benefits of using e‐documents.
The best applications, policies, and procedures are of little use if users do not know how to use them. That leads us to the next step in this framework: training.
Educate and Train Users
Users should have the opportunity to learn how to make the most of e‐document technologies provided to them. In addition to the typical training on the mechanics of using a desktop application (for example, opening, saving, editing, and so on), we should point out features that may not be immediately apparent, such as:
- How to use e‐document features to collaborate with colleagues
- The security features provided with the e‐document system and how (and why) to use them
- How e‐documents, workflows, and collaboration tools may be used to support other business objectives, such as enterprise‐wide green initiatives
Education programs should continue over an extended period of time. As users learn how to use the features of e‐document technology and become familiar with its capabilities, they may come up with new and innovative uses for the technology. Of course, an ideal use of collaboration features of e‐document systems is for sharing training material and collecting feedback from users in the form of reviewers' comments.
Monitor and Tune
The final step in the framework is monitoring and tuning. Here is a case where integrated management reporting will be useful for identifying problem areas, such as:
- Bottlenecks and inefficient operations. Are there parts of workflows that take much longer than other steps? Are some user's queues of documents to review much longer than others?
- Compliance problems. Are documents properly archived? Are some types of documents or documents from some departments more likely to generate quality control problems?
- Workflows that could be more effectively performed if merged with other workflows. For example, could separate requisition processing workflows in operating units and in central purchasing be more efficient if they were combined into a single workflow? As noted earlier, care must be taken not to introduce unintended consequences when merging. Modeling a workflow and walking through typical and atypical use cases can help uncover potential problems.
E‐document systems can support complex business processes; even the most automated workflow can run into problems over time. Start with basic management reports to ensure system managers and workflow managers have a reasonable picture of the state of the system and their business processes. As they gain experience with the system and the reports, they may be able to fine tune the reporting for their business' particular needs.
Conclusion
This guide highlights ways businesses, governments and other organizations can make use of e‐document technology to make operations more efficient. This process starts by understanding the challenges to efficient collaboration (described in Chapter 1) and ranges from the pervasive need for content creation to the challenges of the evolving ways we share information. Although documents and collaboration are ubiquitous, different types of organizations have different needs. Chapter 2 considered how organizations in diverse areas such as life sciences, financial services, manufacturing, and government can all benefit from e‐document technology. A variety of collaboration and information exchange applications are available today and the technical aspect of those were discussed in Chapter 3.
In this chapter, we turned our attention to the management aspects of collaboration and information exchange. Both formal and informal information exchanges can be supported by e‐document technology; however, software alone is not enough to guarantee success. Sound planning and management procedures, such as those described earlier, are required to ensure e‐document technology is used in ways that support business operations, remain operational over extended periods of time, and are adopted by the users they are designed for. Existing technologies can improve productivity and cost savings within organizations but only if both the proper technology and management practices are in place.