Maintain the Integrity of Election Systems
Business Drivers
In the United States, state and local governments are responsible for maintaining democratic processes by ensuring the availability and resilience of election systems, the integrity and accuracy of balloting and vote tabulation, and the confidentiality of individual citizens' votes.
With the responsibility to conduct and run the vote in their areas, secretaries of these boards of elections must guard the public's trust in the voting system by:
- Presenting citizens with opportunities to exercise their right to vote.
- Providing secure facilities and infrastructure for the voting process.
- Ensuring the integrity of the votes themselves.
- Protecting citizens' private data, including information in voter registration databases and other related data repositories.
- Meeting federal and state regulatory requirements.
Business Problem
Since the Department of Homeland Security, or DHS, deemed election systems critical infrastructure in January 2017, state and local boards of elections are taking additional steps to ensure the integrity of the vote at every level. DHS defines election infrastructure as:
- Voter registration databases
- IT infrastructure and systems used to manage elections
- Voting systems
- Storage systems for election and voting infrastructure
- Polling places, including early voting locations
Many states and localities have had electronic voting machines in service for more than a decade, which is beyond their original life expectancy. Moreover, the voting machines and other voting system components often reside on unsegmented networks that do little to minimize exposure and security risks, potentially leaving the voting process vulnerable to cyberattacks. Reported high-profile attacks on recent elections have elevated the importance of better cybersecurity. Elections officials must guard their aging infrastructure against denial of service, unauthorized access, and attempts to alter or exfiltrate data, in addition to motivated hacktivists and nation-states with access to increasingly sophisticated tools.
State and local governments are now addressing voting systems vulnerabilities with grants available through the Consolidated Appropriations Act, 2018. The first step is to understand what exposures exist with current voting machines and all related systems. Then, governments can focus on the approaches they will take to prevent successful cyberattacks and unauthorized data access. As they upgrade voting infrastructure, they must ensure their cybersecurity approaches will continue to defend against threats, thereby maintaining availability and the public's trust.
Traditional Approaches to Cybersecurity for Election Systems
As cyberthreats to digital election systems have increased, state and local governments have placed greater emphasis on election security. As several breaches have demonstrated, traditional approaches have fallen short in multiple different ways.
Reliance on Isolated or Perceived "Air-Gapped" Environments to Bolster Security
Air-gapped or isolated information systems are not inherently secure. Although isolated information systems may not directly communicate with the internet, they are often exposed to internal networks in some way. For example, some voting machines use individually keyed USB drives to tabulate votes. Poll workers plug these drives into endpoints that transmit voting results over a network to a server for tabulation. This transmission introduces risk to the process, exposing election systems' management computers to attack from the local network. Also, insiders with local network access may maliciously or inadvertently access, expose, or even tamper with election data. Finally, since aging voting machines and their management systems are often no longer supported, out-of-date relative to patches and antivirus, and lack OS hardening, they are more vulnerable to cyberattacks.
Creation of Too Much Management Overhead
Governments have typically created multilayered approaches to cybersecurity by adding more products to their infrastructure. Whether to protect against network intrusions; secure web browsing, laptops or cloud-based applications; or perform other functions, maintaining multiple siloed security products drives up costs and requires more management overhead. Since these products can't easily coordinate their threat insights, IT and security teams must either manually stitch together threat intelligence feeds and their updates or have incomplete threat visibility. This approach lacks the automated, swift prevention needed to be effective.
Offering Incomplete Visibility
Related to incomplete threat views, most governments have little visibility into traffic or applications on their networks, let alone which users access which systems. In the event of malicious or inadvertent access to election systems, many state and local governments have no way of detecting it. For example, some assessments of election management servers have found remote access software installed on them, often without the knowledge of the government IT teams.
Guidance from the U.S. Election Assistance Commission and Department of Homeland Security for Election Systems Security
To improve security for election systems, the U.S. Election Assistance Commission, or EAC, has federal grants available through the Consolidated Appropriations Act of 2018, which includes funds to implement established cybersecurity best practices for election systems as well as fund other activities that will improve the security of elections for federal office. Secretaries of state have authority and administration responsibility for federal grants provided by the EAC, but local election commissions and their officers have authority for execution and implementation of the election process, including transmission of voting data.
The EAC also released a set of principles and guidelines for voting systems. As you build your cybersecurity approach, consider how it will cover the principles set forth by the federal government, which include:
- System integrity: The voting system should perform its intended function in an unimpaired manner, free from unauthorized manipulation of the system, whether intentional or accidental. Guidelines stipulate that the voting system should use multiple layers of controls to provide redundancy against security failures or vulnerabilities; limit its attack surface by reducing unnecessary code, data paths and physical ports, as well as by using other technical controls; and maintain as well as verify the integrity of software, firmware, and other critical components.
- Detection and monitoring: The voting system should provide mechanisms to detect anomalous or malicious behavior by recording important activities through event logging mechanisms, which are stored in a format suitable for automated processing; generating, storing and reporting all error messages as they occur; employing mechanisms to protect against malware; and ensuring any voting system with networking capabilities employs appropriate, well-vetted modern defenses against network-based attacks, commensurate with current best practices.
- Access control: The voting system should include default access control policies that enforce the principles of least privilege and separation of duties; support multi-factor authentication, or MFA; and limit the access of users, roles and processes to the specific functions and data to which each entity holds authorized access.
Palo Alto Networks Approach to Securing Election Systems Infrastructure
The Palo Alto Networks® Security Operating Platform helps state and local governments reduce cybersecurity risk for election systems as well as meet regulatory requirements with coordinated, consistent and automated threat prevention across endpoints, networks and cloud environments. State and local governments have chosen the Security Operating Platform to:
- Improve threat prevention response times with analytics and automation: Timing is critical in elections. Keeping up with the latest malware and exploits is a full-time job for network and security teams, and it's not enough to detect – cybersecurity must prevent. The Security Operating Platform prevents successful cyberattacks through automation. WildFire® malware prevention service identifies new threats discovered anywhere in the world, creates new protections against them and automatically distributes them to all security enforcement points, across the network, clouds and endpoints, in as few as five minutes. In addition, MineMeld™ threat intelligence syndication engine extracts indicators of compromise from threat intelligence feeds, such as those from DHS and the MS-ISAC. MineMeld compiles the indicators into multiple formats compatible with Palo Alto Networks next-generation firewalls – as well as other security and information event management, or SIEM, platforms – for swift and automated prevention.
- Enforce Zero Trust in networks that house critical infrastructure: Implementing a Zero Trust network architecture allows election officials to limit the attack surface by isolating internal network segments that house elections data as well as controlling which employees, applications and traffic can access the segment. The Security Operating Platform enforces Zero Trust by virtually segmenting the network and granting access to segments based on an employee's device, application requested and job function, denying all other u nnecessary access. Network or security teams can create and enforce granular policies that lock away critical infrastructure access from all but certain users and groups – rather than IP addresses or ports – and help them quickly identify any anomalous use. For example, you can put restrictions on the type of data that can leave network segments and specify which traffic flows should be decrypted. Zero Trust adds another layer of access control security, beyond usernames and passwords: teams can enforce MFA, specify the security posture of devices accessing the segments and require clientless VPN for secure remote access.
- Protect critical endpoints: Traps™ advanced endpoint protection is particularly suited for endpoints on isolated networks, such as voting machines. It employs a multi-method approach to blocking exploits, ransomware and other malware, and fileless attacks. Traps protects numerous devices and operating systems and is self-sufficient, not reliant on outbound connectivity to identify or prevent known threats.
- Protect legacy devices: Traps also supports old operating system versions, making it ideal for protecting legacy servers for which software patches are no longer available.
Actual Customer Implementation
Palo Alto Networks secures election systems infrastructure at state and local government levels, as detailed in the following example. This customer, a department of state, took a holistic approach to election systems security across several critical areas of its network.
Secure the Voter Registration Database and Related Systems
To preserve the integrity of its election systems infrastructure, the department focused on protecting the voter registration database, including the voter registration process, at each link of the verification chain. The voter registration database is housed in the department's data center and must connect with other systems during the voter registration process. When a person registers to vote, a series of transactions takes place with databases belonging to other governmental agencies to verify that person's eligibility:
- Department of State verifies the person has not already registered as a voter.
- Department of Motor Vehicles verifies the person's home address.
- Department of Correctional Services verifies the person is not currently incarcerated or on parole.
- Department of Health verifies the person has not been reported as deceased.
To address security needs across these systems, the department deployed Palo Alto Networks next-generation firewalls at the core of its data center. Using the insights gleaned from the application and user network activity visible through the firewall, the department's team segmented the data center network to minimize risk. Taking advantage of the integration with user directories through the firewall's User-ID™ technology, the team built policies to ensure only authorized employees could access network segments that house election systems. Authorizing only specific applications, users and traffic patterns in and out of certain network segments reduces risk while the platform continually scans for new threats and logs unapproved traffic flows for analysis.
Protect the Entire Network and Blocking Credential Theft
Taking a phased approach, the department's team began using the next-generation firewalls at the network perimeter. Palo Alto Networks next-generation firewalls employ integrated credential theft prevention and other features to block even the most sophisticated phishing emails, links and malicious websites from duping state officials into relinquishing their credentials. This is a particularly important step since it's been reported that credential theft was a key element in the successful attacks that attempted to interfere with the 2016 U.S. election.
The next-generation firewall identifies and blocks attempts to steal credentials by stopping the submission of valid corporate or government credentials to illegitimate websites. Through integration with identity and access management technologies, the firewall can enforce MFA at the network layer, neutralizing an attacker's ability to use stolen credentials for lateral movement. MFA adds a layer of protection to meet DHS recommendations while providing peace of mind by limiting the value of stolen credentials.
Protect Departmental Web Presence
The firewalls also protect public-facing departmental websites, ensuring the integrity of the election information citizens rely upon as well as preventing defacement or unauthorized alteration of polling places, hours of operation and reported election results. All firewalls are centrally managed by Panorama™ network security management.
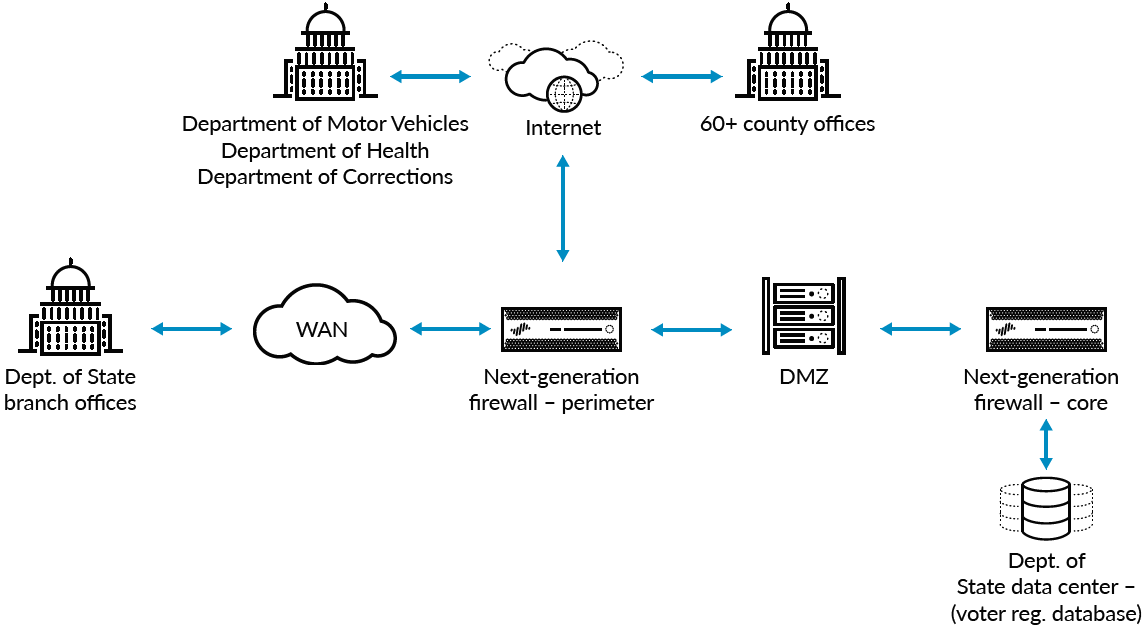
Figure 1: High-level state data center diagram
Maintain Security Across 60 Counties
The challenge for state officials lies in the coordination with more than 60 counties on Election Day. The state Board of Elections maintains the voter registration database and provides access to local boards of elections to enable citizens to cast a ballot. The counties share a common network backbone with the state for access to shared resources. Palo Alto Networks firewalls installed at the perimeter provide automated threat prevention and complete visibility of network traffic in and out of the state data center, branch offices and counties. Since the firewalls are automatically updated with protections against the latest malware, exploits, malicious URLs and other threats, protection scales with minimal administrative overhead, allowing network staff to focus on innovation.
Products
- PA-3060 (3), PA-5050 (4) with Threat Prevention, URL Filtering and WildFire subscriptions
- Panorama M-100 (2)
Services
A resident engineer focuses on how an organization can best implement the capabilities of the Security Operating Platform to meet business, operational and security goals. In this instance, a resident engineer helped the state department's team transition its network to a Zero Trust architecture that takes advantage of user, application and content visibility to reduce cyber risk.
Considerations for Election Day and Beyond: A Comprehensive Security Strategy
A comprehensive security strategy for election systems does not stop at the data center or at the perimeter of the network. An effective security posture addresses any potential vulnerable area of the network.
Voting Machines, Critical Systems and Their Management Servers; Mobile Devices and Temporary Technology Deployments
To meet federal recommendations and guidelines, the aforementioned Department of State can replace the traditional antivirus software on its voting systems and management server with Traps advanced endpoint protection, which works whether endpoints are online or offline, on the network or off. As part of the overall platform, Traps coordinates enforcement with Palo Alto Networks next-generation firewalls, benefiting from shared analysis and automation across network and endpoints to stop malware, exploits and ransomware before they compromise these systems. WildFire delivers the latest protections to endpoints in as few as five minutes following discovery of an attack, anywhere in the world. This reduced risk is even more crucial for critical systems that lack patches and security hardening or are no longer supported by their manufacturers.
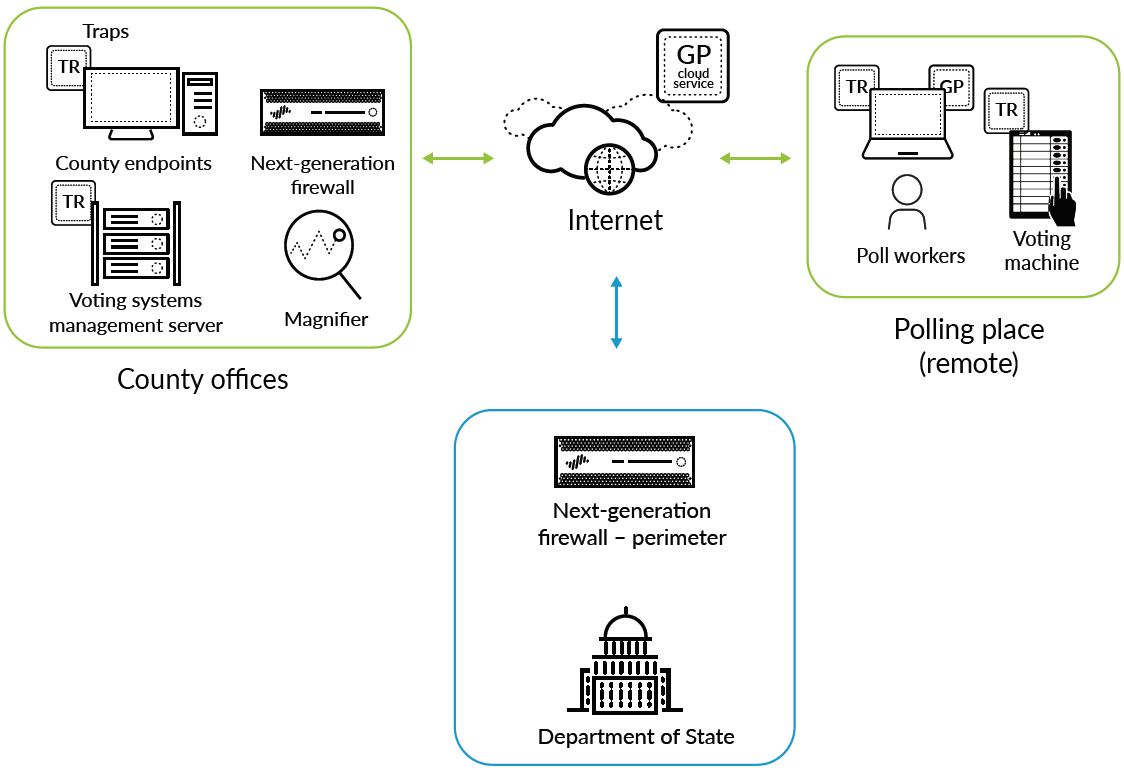
Figure 2: Election Day deployment
Election Day Infrastructure Communications
Election workers deploy voting systems and endpoints at remote locations throughout communities on Election Day. By extending the same level of protection to every location, state teams can reduce risk at any potentially vulnerable point of the election systems. GlobalProtect™ network security for endpoints, through GlobalProtect cloud service, extends an IPsec VPN and existing security policies from the data center and network out to remote locations, such as county offices and polling stations. GlobalProtect cloud service enables consistent security across Election Day infrastructure to help ensure the integrity of the vote. The Department of State's team can manage GlobalProtect cloud service through Panorama, and with no hardware to set up, the service deploys in hours – ideal for transient polling stations. GlobalProtect cloud service harnesses the same shared threat intelligence as the rest of the Security Operating Platform, preventing successful cyberattacks on voting systems and results.
Behavioral Analytics
States can choose to add another layer of prevention through Magnifier™ behavioral analytics. The data flow for the voter registration process and voting on Election Day are transaction-based and predictable. By analyzing rich network, endpoint and cloud data with machine learning, Magnifier accurately identifies targeted attacks, malicious insiders and malware. State or county IT teams can investigate potential threats, including those within the organization, and take advantage of the Security Operating Platform to scrutinize unusual behavior as well as block attacks, protecting the integrity of the voting process.
Benefits of Palo Alto Networks for Election Systems Infrastructure
With a comprehensive security strategy using the Palo Alto Networks Security Operating Platform, officials of state and county boards of elections will be able to focus on what matters most – Election Day – instead of the administration or management of technology. This state department, along with many others throughout the U.S. and the world, entrusts Palo Alto Networks to help prevent successful cyberattacks on critical systems, including election systems infrastructure. The platform is helping this department prevent threats across its statewide data center, the county network, voter registration databases, endpoints and remote systems. Following the Palo Alto Networks approach for securing election systems, other state and local governments can enjoy a multitude of benefits, including:
Business Benefits
- Ensure faith and confidence in the voting process, tabulation and results reporting.
- Meet U.S. Senate Intelligence Committee and DHS recommendations.
- Align with guidelines from appropriate entities, including NIST, the Center for Internet Security and the Election Infrastructure Subsector Government Coordinating Council.
Operational Benefits
- Reduce risk and improve cybersecurity coordination between network, security and desktop teams by sharing complete user and application visibility across networks, endpoints, users and devices, including users and devices outside organizational boundaries.
- Reduce cybersecurity management overhead by automatically updating security enforcement points with protections against the latest threats.
Security Benefits
- Protect unpatched voting machines as well as reporting and tabulation systems with advanced endpoint protection.
- Limit exposure of the voter registration database with network segmentation.
- Prevent credential theft and data exfiltration through coordinated web filtering and traffic inspection.
- Enforce Zero Trust with User-ID and MFA.